Difference between revisions of "Audit Log"
imported>Aeric |
Wikidevuser (talk | contribs) |
||
| (10 intermediate revisions by one other user not shown) | |||
| Line 6: | Line 6: | ||
The Audit Log tracks the following actions: | The Audit Log tracks the following actions: | ||
:* All changes to data (additions, modifications and deletions) | :* All changes to data (additions, modifications and deletions) | ||
:* | :* All customizations to the platform, including | ||
::* Changes to [[Access Controls]] | |||
::* Changes in [[User]] assignments | |||
::* Changes to [[Object]] configurations | |||
::* Changes to [[Classes]] and JSP [[Pages]]<br>and so on... | |||
===Web Service Executions=== | ===Web Service Executions=== | ||
| Line 16: | Line 20: | ||
===Enhanced Security Audit=== | ===Enhanced Security Audit=== | ||
Optionally, an [[#Enhanced Security Setting|Enhanced Security]] can be enabled, increasing the audit scope to log: | |||
:*All record access attempts | :* All record access attempts | ||
:*Unsuccessful or unauthorized access attempts | :* Unsuccessful or unauthorized access attempts | ||
[[ISV]]s also have a [[Global Audit Log]] they can use to track information from all tenants. | [[ISV]]s also have a [[Global Audit Log]] they can use to track information from all tenants. | ||
| Line 38: | Line 42: | ||
#Click the ''Next'' link to view additional log pages. | #Click the ''Next'' link to view additional log pages. | ||
#To change the sort order, click a column heading. | #To change the sort order, click a column heading. | ||
'''Viewing Entries:''' | |||
:* For additional information on a Web Service entry, click the '''View Details''' link that accompanies it. | |||
:* Long entries are truncated. Click '''Show more''' to expand one. Click '''Show less''' to collapse it again. | |||
===Create an Audit Log View=== | ===Create an Audit Log View=== | ||
| Line 62: | Line 70: | ||
===Filter the Audit Log=== | ===Filter the Audit Log=== | ||
Find activity history (Audit Log): | Find activity history (Audit Log): | ||
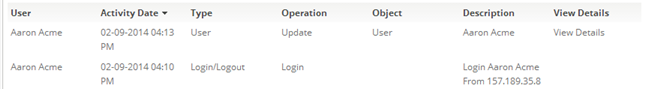
#Click '''[[File:GearIcon.png]] > Administration > Monitoring > Audit Log'''.<br>The Audit Log page opens and displays a list of activity records. | #Click '''[[File:GearIcon.png]] > Administration > Monitoring > Audit Log'''.<br>The Audit Log page opens and displays a list of activity records. like this one: | ||
#:[[File:AuditLog.png]] | |||
#Use the Filter icon [[File:DoubleDownIcon.png]] to determine which records are listed: | #Use the Filter icon [[File:DoubleDownIcon.png]] to determine which records are listed: | ||
#:''Learn more:'' [[Views]] | #:''Learn more:'' [[Views]] | ||
===Enhanced Security | ===Enhanced Security Setting=== | ||
#Click '''[[File:GearIcon.png]] > Administration > Company Information > Edit''' | #Click '''[[File:GearIcon.png]] > Administration > Company Information > Edit''' | ||
| Line 97: | Line 106: | ||
To configure Auto-Purge for Audit Log records: | To configure Auto-Purge for Audit Log records: | ||
#Click '''[[File:GearIcon.png]] > Administration > Monitoring > Audit Logs''' | #Click '''[[File:GearIcon.png]] > Administration > Monitoring > Audit Logs''' | ||
#Click the '''[ | #Click the '''[Retention Period]''' button | ||
#Specify the number of days to retain the Audit Log entries | #Specify the number of days to retain the Audit Log entries | ||
#:The number of days must be a positive number, greater than zero | #:The number of days must be a positive number, greater than zero | ||
Latest revision as of 12:26, 15 June 2023
![]() > Administration > Monitoring > Audit Log
> Administration > Monitoring > Audit Log
Audit logs display a full history of actions in the platform.
About the Audit Log
The Audit Log tracks the following actions:
- All changes to data (additions, modifications and deletions)
- All customizations to the platform, including
- Changes to Access Controls
- Changes in User assignments
- Changes to Object configurations
- Changes to Classes and JSP Pages
and so on...
Web Service Executions
When Web Services are integrated into an application, the Audit Log contains the following:
- All Web Service execution failures
- Successful executions of any Web Services that have the Debug flag set in the Service Parameters
In each case, you click View Details' on the audit log entry to see the request including the URL, header parameters, and input parameters. Output parameters are also displayed and, in the case of an error, a stack trace.
Enhanced Security Audit
Optionally, an Enhanced Security can be enabled, increasing the audit scope to log:
- All record access attempts
- Unsuccessful or unauthorized access attempts
ISVs also have a Global Audit Log they can use to track information from all tenants.
Working with the Audit Log
- Users with the Manage Audit Log permission enabled can:
- Users with Customize Objects permission can create Field Audit Logs
View an Audit Log
- Click
 > Administration > Monitoring > Audit Log.
> Administration > Monitoring > Audit Log.
The Audit Log page opens and displays a log of activities by user.
These fields are displayed in the Audit Log:- Activity Date
- Description
- Object
- User
- Click the Next link to view additional log pages.
- To change the sort order, click a column heading.
Viewing Entries:
- For additional information on a Web Service entry, click the View Details link that accompanies it.
- Long entries are truncated. Click Show more to expand one. Click Show less to collapse it again.
Create an Audit Log View
To create a new view of user activities:
- Click
 > Administration > Monitoring > Audit Log.
> Administration > Monitoring > Audit Log.
The Audit Log page opens and displays a log of activities by user. - Click the View Icon, and select New View from the drop-down list.
The Create Audit Log View page opens. The default setting includes the four columns available for the log view: User, Activity Date, Object, and Description.- To remove any of the default columns from the new view, select the column name in the Selected Columns list, and click the left-arrow button .
- If there are entries in the Available Columns list that you want to include in the new view, select them and click the right-arrow button .
- Rearrange the Selected Columns, as necessary, by clicking the up and down arrow buttons.
- Select the column by which you want to First Sort By, then the Sort Order.
- Choose a second sort criteria and sort order, if desired.
- Select the Visibility option you want to apply to this view:
- Visible Only to Me
- The view appears only in your own View list.
- Visible to Everyone
- The view appears in the View list for all users in your company.
- Visible to Specific Users
- The view appears in the View list only for the users you select. When you select this option, a text box and Lookup button appear. Click the button and select the users you want to have access to this view. You can remove users by clicking the Remove button .
- Visible to Specific Roles
- The view appears in the View list only for users with roles that you specify. Click the Lookup button to select the roles you want to have access to this view. You can remove roles by clicking the Remove button.
- Visible to Specific Teams
- The view appears in the View list only for users that belong to teams that you specify. Click the Lookup button to select the teams you want to have access to this view. You can remove teams by clicking the Remove button.
- Click [Preview] to see the new view.
- Click [Save] to save the view without setting up filters
-OR-
Enter a View Name, and click [Save As]
-OR- - Click the Filter tab to complete the new custom log view, and save your changes.
- See Views for more information.
Filter the Audit Log
Find activity history (Audit Log):
- Click
 > Administration > Monitoring > Audit Log.
> Administration > Monitoring > Audit Log.
The Audit Log page opens and displays a list of activity records. like this one: - Use the Filter icon
 to determine which records are listed:
to determine which records are listed:
- Learn more: Views
Enhanced Security Setting
- Click
 > Administration > Company Information > Edit
> Administration > Company Information > Edit - In the Logging All Access Settings section, choose the preferred log options:
- Log All Record Access
- If enabled, any record access, including search, is logged
- Log All Access Violations
- If enabled, any access violation is logged
- Most access violations occur when a user attempts to access an element in the platform, but does not have the appropriate permission, and so an error message is triggered; Some examples are: You do not have the permission to access this record, Invalid access, You do not have permission for this operation
Delete an Audit Log
Records in an Audit Log can be deleted using the Mass Delete Data feature.
Auto-Purge the Audit Log
This option provides the ability to configure an automatic data purge of the Audit Log, based on some number of days. All audit log entries older than the specified number days are purged automatically.
Users that have the Manage Audit Log permission can configure auto-purge settings
When the auto-purge option is specified, for example with a retention period of 10 days, then any record in the Audit Log that is more than 10 days old is permanently deleted. The auto-purge action may not happen immediately, but the purge action is scheduled every day.
- Considerations
-
- In a purge action, the audit log entries are deleted permanently and cannot be restored
- The auto-purge action bypasses any Recycle Bin restore option
- By default, auto-purge is disabled
To configure Auto-Purge for Audit Log records:
- Click
 > Administration > Monitoring > Audit Logs
> Administration > Monitoring > Audit Logs - Click the [Retention Period] button
- Specify the number of days to retain the Audit Log entries
- The number of days must be a positive number, greater than zero
- If the number of days is equal to zero, Auto-Purge is disabled
- Field label
- Retention Period (Days)
- Click [Save]
The Audit Log includes a log of any actions related to Auto-purge settings.