Difference between revisions of "Delegated Authentication"
imported>Aeric m (Text replace - 'Settings > ' to 'File:GearIcon.png > Setup > ') |
imported>Aeric |
||
| (16 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
With delegated authentication, you use your own server to validate platform | With delegated authentication , you can use your own server to validate platform users against a corporate database or an LDAP Directory. You can use a single username and password to access all applications as long as the applications support delegated authentication. | ||
===Scope === | ===Scope === | ||
Delegated | Delegated authentication is limited to user authentication and does not include authorization. You must be active in the platform, and teams, roles, and other permissions must also be maintained. | ||
The corporate System Administrator or the IT Staff develop and implement a web service that can accept and respond to the web service calls made by the platform servers. | |||
=== | ===Working with delegated authentication=== | ||
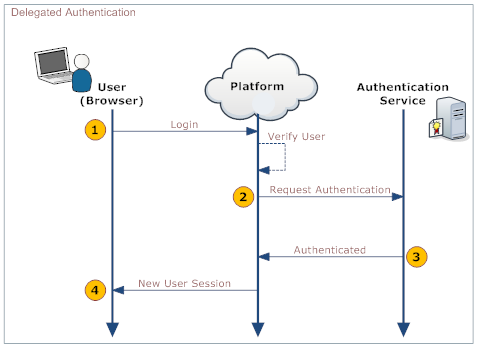
When | When you logon to the platform, your identity is authenticated in the platform and on your organization's systems. The following diagram shows the process: | ||
:[[File:SSO-DA.png]] | :[[File:SSO-DA.png]] | ||
This table describes the actions taken by the | This table describes the actions taken by the user, the platform, and your organization's [http://en.wikipedia.org/wiki/Web_service Web Service]. | ||
:{| border="1" cellpadding="5" cellspacing="0" | :{| border="1" cellpadding="5" cellspacing="0" | ||
| Line 16: | Line 16: | ||
!User | !User | ||
!Platform | !Platform | ||
!Your | !Your organization's web service | ||
|- | |- | ||
|1. || Log | |1. || Log on the platform || Validate that: | ||
:* User is | :* User is active | ||
:* SSO is | :* SSO is enabled | ||
| | | | ||
|- | |- | ||
|2. || || Make a | |2. || || Make a web services call to the organization's web service, requesting authorization. | ||
Include | Include the following parameters in the call: | ||
:<syntaxhighlight lang="java" enclose="div"> | :<syntaxhighlight lang="java" enclose="div"> | ||
username | username | ||
| Line 30: | Line 30: | ||
originatingIp | originatingIp | ||
</syntaxhighlight> | </syntaxhighlight> | ||
''Note:'' originatingIp is the IP address that | ''Note:'' originatingIp is the IP address that initiates the login request. This could be useful to restrict access based on the user's location. The web service must be implemented in a way that the platform is able to access it. | ||
| | | | ||
|- | |- | ||
| Line 38: | Line 38: | ||
|} | |} | ||
===Enabling | ===Enabling delegated authentication=== | ||
#Click '''[[File:GearIcon.png]] > | #Click '''[[File:GearIcon.png]] > Administration > Account Management > Single Sign-On Settings'''. | ||
#Click the '''[Edit]''' button | #Click the '''[Edit]''' button. | ||
# | #Choose '''Delegated Authentication''' from the ''Single Sign-On Using'' drop-down list. | ||
# | #Specify the URL of the authentication server running in your environment (abc5.abc.com:8080) in the ''SSO Gateway Url'' field. | ||
#:Note that the URL and Port number must be specified using a [http://en.wikipedia.org/wiki/FQDN Fully Qualified Domain Name] or an IP address. Secure HTTPS (Hypertext Transfer Protocol over Secure Socket Layer) protocol is used to access this URL. If you do not have this information available, contact your IT department or System Administrator. | |||
#:Note that the URL and Port number must be specified using a [http://en.wikipedia.org/wiki/FQDN Fully Qualified Domain Name] or an IP address. Secure HTTPS (Hypertext Transfer Protocol over Secure Socket Layer) protocol is used to access this URL. | #Choose whether or not to enable SSO for individual [[User]]s. | ||
# | |||
#Click '''[Save]''' | #Click '''[Save]''' | ||
===Setting up | ===Setting up communication with the authentication server=== | ||
The authentication server needs a certificate for a successful handshake with the platform. If you are using a self-signed certificate, it needs to be loaded into the cacert keystore file in the platform's <tt>{installed_JDK}/jre/lib/security</tt> folder. Unable to load the certificate displays an SSL error. | |||
To load the certificate into the keystore: | To load the certificate into the keystore: | ||
# | # Check the configuration in the following three locations: | ||
#:* <tt>installation.properties</tt> | #:* <tt>installation.properties</tt> | ||
#:* <tt>configure.pl</tt> installation script | #:* <tt>configure.pl</tt> installation script | ||
#:* <tt>scripts/longjump</tt> | #:* <tt>scripts/longjump</tt> | ||
#: | # Make sure that the <tt>JAVA_HOME</tt> environment variable points to the JRE in the installed JDK. | ||
# Load the certificate using the <tt>keytool -import</tt> command | #: For more information, see Platform [[Installation Files]]. | ||
#: The default password is | # Load the certificate using the <tt>keytool -import</tt> command. | ||
#: '''Note:''' The default password is '''changeit'''. | |||
For more information , see [http://download.oracle.com/javase/tutorial/security/toolsign/rstep2.html Java Tutorial: Importing a Certificate]. | |||
===Making a web service call=== | |||
===Web | Use the URL and port number provided under the ''Single Sign-On Settings'' section to make a SOAP request to authenticate the users. SSO Request and SSO Response are predefined by the platform. These request and response are conducted via SOAP messaging. | ||
===Web services message format=== | |||
;Request:SSO SOAP Request sent from the platform is as follows: | ;Request:SSO SOAP Request sent from the platform is as follows: | ||
:<syntaxhighlight lang="xml" enclose="div"> | :<syntaxhighlight lang="xml" enclose="div"> | ||
Latest revision as of 08:58, 9 March 2017
With delegated authentication , you can use your own server to validate platform users against a corporate database or an LDAP Directory. You can use a single username and password to access all applications as long as the applications support delegated authentication.
Scope
Delegated authentication is limited to user authentication and does not include authorization. You must be active in the platform, and teams, roles, and other permissions must also be maintained.
The corporate System Administrator or the IT Staff develop and implement a web service that can accept and respond to the web service calls made by the platform servers.
Working with delegated authentication
When you logon to the platform, your identity is authenticated in the platform and on your organization's systems. The following diagram shows the process:
This table describes the actions taken by the user, the platform, and your organization's Web Service.
User Platform Your organization's web service 1. Log on the platform Validate that: - User is active
- SSO is enabled
2. Make a web services call to the organization's web service, requesting authorization. Include the following parameters in the call:
- <syntaxhighlight lang="java" enclose="div">
username password originatingIp </syntaxhighlight> Note: originatingIp is the IP address that initiates the login request. This could be useful to restrict access based on the user's location. The web service must be implemented in a way that the platform is able to access it.
3. Validate the passed information and return either "Authenticated" or "Failure". 4. On Authenticated response, generate a new User Session. On Failure, notify the user.
Enabling delegated authentication
- Click
 > Administration > Account Management > Single Sign-On Settings.
> Administration > Account Management > Single Sign-On Settings. - Click the [Edit] button.
- Choose Delegated Authentication from the Single Sign-On Using drop-down list.
- Specify the URL of the authentication server running in your environment (abc5.abc.com:8080) in the SSO Gateway Url field.
- Note that the URL and Port number must be specified using a Fully Qualified Domain Name or an IP address. Secure HTTPS (Hypertext Transfer Protocol over Secure Socket Layer) protocol is used to access this URL. If you do not have this information available, contact your IT department or System Administrator.
- Choose whether or not to enable SSO for individual Users.
- Click [Save]
Setting up communication with the authentication server
The authentication server needs a certificate for a successful handshake with the platform. If you are using a self-signed certificate, it needs to be loaded into the cacert keystore file in the platform's {installed_JDK}/jre/lib/security folder. Unable to load the certificate displays an SSL error.
To load the certificate into the keystore:
- Check the configuration in the following three locations:
- installation.properties
- configure.pl installation script
- scripts/longjump
- Make sure that the JAVA_HOME environment variable points to the JRE in the installed JDK.
- For more information, see Platform Installation Files.
- Load the certificate using the keytool -import command.
- Note: The default password is changeit.
For more information , see Java Tutorial: Importing a Certificate.
Making a web service call
Use the URL and port number provided under the Single Sign-On Settings section to make a SOAP request to authenticate the users. SSO Request and SSO Response are predefined by the platform. These request and response are conducted via SOAP messaging.
Web services message format
- Request
- SSO SOAP Request sent from the platform is as follows:
- <syntaxhighlight lang="xml" enclose="div">
<?xml version="1.0" encoding="UTF-8" ?> <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Body> <LJAuthenticate xmlns="urn:authentication.soap.ws.longjump.com"> <username>jim@abc.com</username> <password>sales</password> <originatingIp>1.2.3.4</originatingIp> </LJAuthenticate> </soapenv:Body> </soapenv:Envelope> </syntaxhighlight>
- Response
- SSO SOAP Response expected by the Platform is as follows:
- <syntaxhighlight lang="xml" enclose="div">
<?xml version="1.0" encoding="UTF-8" ?> <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Body> <LJAuthenticateResponse xmlns="urn:authentication.soap.ws.longjump.com"> <Status>Authenticated</Status> </LJAuthenticateResponse> </soapenv:Body> </soapenv:Envelope> </syntaxhighlight>